Amazon Leadership Principles
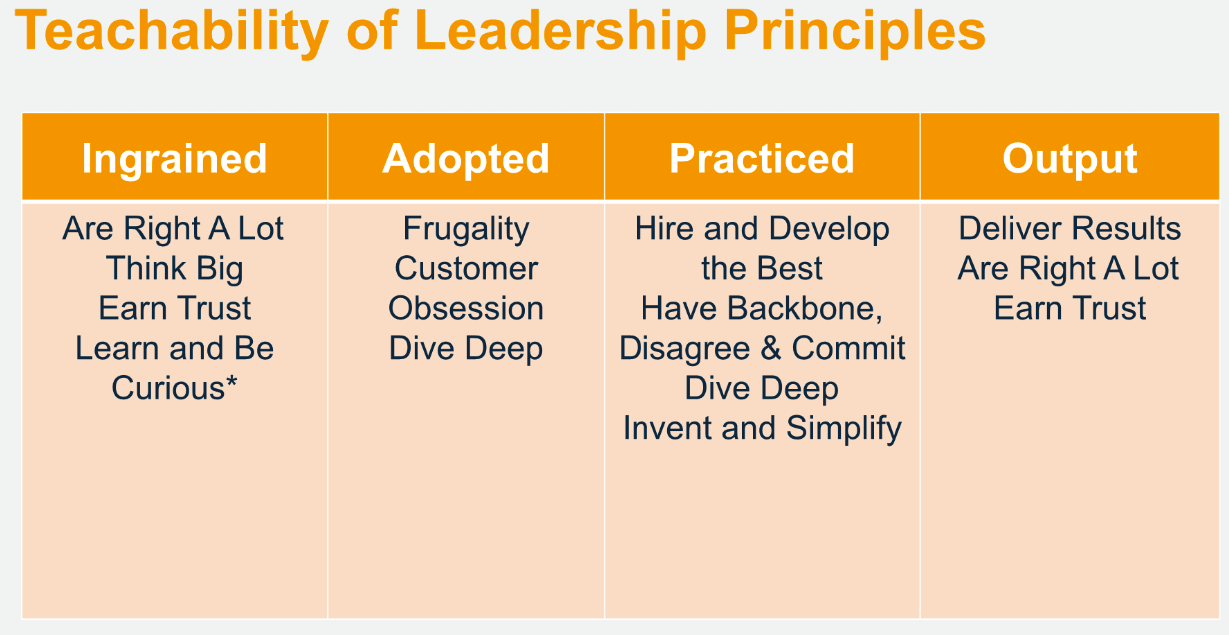
Amazon’s Leadership Principles form the core of the company’s DNA. Some are foundational, others procedural, and all of them reflect essential facets of what it means to be Amazonian. But our Leadership Principles are more than cultural artifacts – they are, in fact, central to how we operate.